Mobile Application Security
Reduce your risk of a breach by identifying and eliminating critical security vulnerabilities across your mobile application ecosystem with on-demand mobile application security testing expertise.


What is a Mobile application security?
Mobile application security focuses on the software security posture of mobile apps on various platforms like Android, iOS, and Windows Phone. This covers applications that run both on mobile phones as well as tablets. It involves assessing applications for security issues in the contexts of the platforms that they are designed to run on, the frameworks that they are developed with, and the anticipated set of users (e.g., employees vs. end users). Mobile applications are a critical part of a business’s online presence and many businesses rely entirely on mobile apps to connect with users from around the world.
All popular mobile platforms provide security controls designed to help software developers build secure applications. However, it is often left to the developer to choose from myriad of security options. A lack of vetting can lead to security feature implementation that can be easily circumvented by attackers.
Common issues that affect mobile apps include:
- Storing or unintentionally leaking sensitive data in ways that it could be read by other applications on the user’s phone.
- Implementing poor authentication and authorization checks that could be bypassed by malicious applications or users.
- Using data encryption methods that are known to be vulnerable or can be easily broken.
- Transmitting sensitive data without encryption over the Internet.
These issues could be exploited in many ways; for example, by malicious applications on a user’s device, or by an attacker who has access to the same WiFi network as an end user.
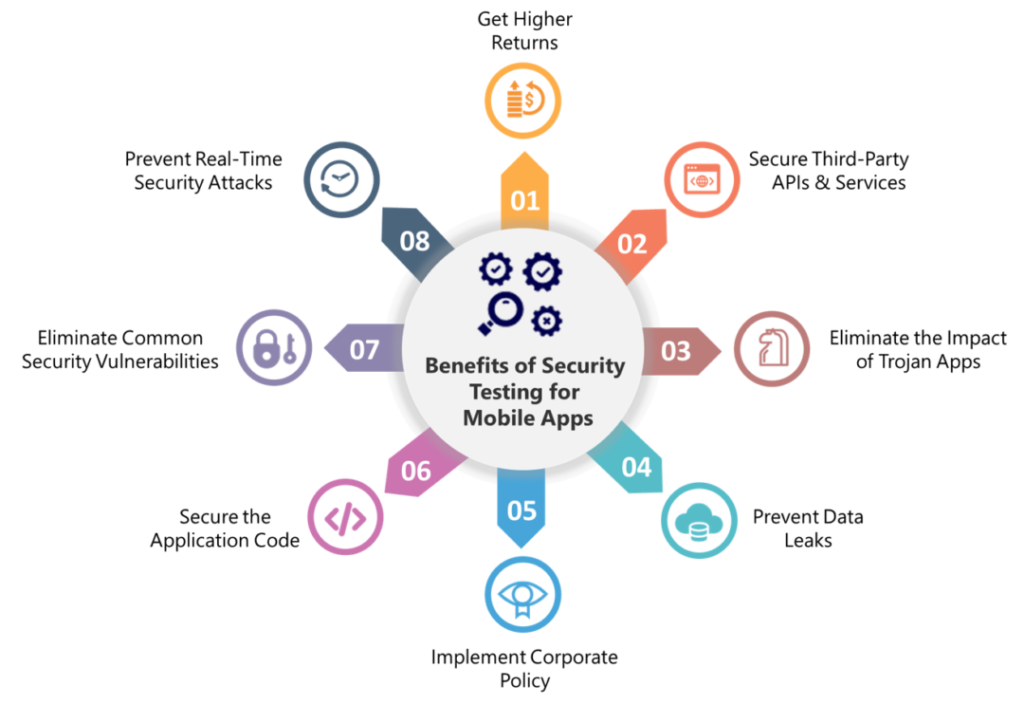
Why Must Each Business Perform Elaborate Security Testing of Mobile Apps?
Eliminate Common Security Vulnerabilities
Secure the Application Code
Prevent Data Leaks
Prevent Real-Time Security Attacks
Eliminate the Impact of Trojan Apps
Get Higher Returns
Implement Corporate Policy
Secure Third-Party APIs & Services

The testing process includes
Interacting with the application and understanding how it stores, receives, and transmits data.
Decrypting encrypted parts of the application.
Decompiling the application and analyzing the resulting code.
Using static analysis to pinpoint security weaknesses in the decompiled code.
Applying the understanding gained from reverse engineering and static analysis to drive dynamic analysis and penetration testing.
Utilizing dynamic analysis and penetration testing to evaluate the effectiveness of security controls (e.g., authentication and authorization controls) that are used within the application.
Overview of Mobile Application Testing Methodology
Mobile Applications can use a variety of technologies and development frameworks, so Pentest People’s exact technical approach to each application may be very different. However, there are certain fundamental areas that are examined, which are as follows:
Assessment Methods We Apply
Our security testing team combines automated and manual approaches to take the full advantage of the vulnerability assessment process.