Vulnerability Assessment
Enhance your IT Security Program with a vulnerability assessment by Fuzzsecurity. We help you discover the weaknesses in your defenses proactively before someone else does.


What is a vulnerability assessment?
A vulnerability assessment is the testing process used to identify and assign severity levels to as many security defects as possible in a given timeframe. This process may involve automated and manual techniques with varying degrees of rigor and an emphasis on comprehensive coverage. Using a risk-based approach, vulnerability assessments may target different layers of technology, the most common being host-, network-, and application-layer assessments.
Vulnerability testing helps organizations identify vulnerabilities in their software and supporting infrastructure before a compromise can take place. But, what exactly is a software vulnerability?
A vulnerability can be defined in two ways:
- A bug in code or a flaw in software design that can be exploited to cause harm. Exploitation may occur via an authenticated or unauthenticated attacker.
- A gap in security procedures or a weakness in internal controls that when exploited results in a security breach.
Key benefits of a Vulnerability Assessment
Identifies at-risk assets
Validates the suitability of security controls
Informs security investments
Provides strategic advice
Enhance blue team effectiveness
Prioritise future investments
Better understand your organisation’s security weaknesses and ensure that future investments deliver the greatest benefit.
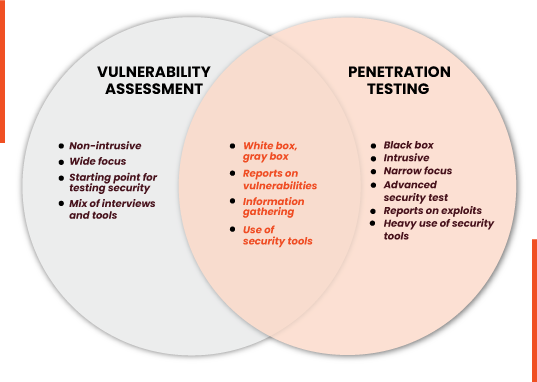
When a vulnerability assessment
could be beneficial
Prior to undertaking a formal compliance audit
Planning an incident response strategy
Writing data and information security policies
Procuring security products and services
FuzzSecurity’s Vulnerability Assessment Services include
Password & Access Management
How are passwords and access management handled? Do people reuse simple passwords? Do you know who has access to what and why, at any time? Can hackers steal employee passwords easily?
Attack Mitigation
We check for mitigation controls for 17 types of cyber attacks: account compromise, unauthorized access, ransomware, network intrusions, malware infections, sabotage, security policy violations, etc.
Security Awareness Training
Has everyone in the organization gotten the appropriate security awareness training? If yes, then do they even remember what was it about? Has its effectiveness been tested?
Cloud Security Assessment
Microsoft 365 has 280+ security settings. Amazon Web Services and Azure have hundreds of security configuration options, too – we will take care of ALL of them!
Securing IT Infrastructure
We help our customers transform their IT infrastructure security by implementing Server & Network Device Hardening, Desktop Hardening, Network & Web Service security, Data Security, Backups, etc.
Vulnerability management
How many vulnerable machines / apps can a company have in its network?
We help our customers establish and manage a Vulnerability management program which will gradually reduce the vulnerabilities in their network.
Penetration Testing
Breach simulation is an integral part of every Information Security Program. Our customers can rely on us to support them in the initiation, execution and conclusion of a Penetration Test.
Secure Software Development
Software development should be a rapid, efficient and secure process. We help our customers integrate security into the design, development, testing, integration and deployment of their code.
Security Policies and Procedures
Policies and Procedures are the governing laws even in a small company’s business. The ones we create are living and breathing documents bringing order and structure to our customers’ security practices.
Secure Remote Access
Secure Work From Home is one aspect of remote access, but we also take care of third party partners and outsourced employees, vendors and guests. Remote access to data is not limited to VPN.
Security Monitoring
Can you detect a policy violation or a security incident in your network today? If you get asked which computers executed unknown scripts or programs in the past 24 hours, can you answer this question?
Network Vulnerability Assessment
Network Vulnerability Assessments usually include enumeration and vulnerability scans. We go deeper by discovering unauthorized access points, weak security configuration settings at your perimeter, and more.
IT infrastructure
- Network. We assess the efficiency of your network segmentation, network access restriction, the ability to connect to the network remotely, firewall implementation.
- Email services. We evaluate the susceptibility to phishing attacks and spamming.
Applications
- Web applications. We assess the susceptibility of a web app to various attacks following Open Web Application Security Project (OWASP) Top 10 Application Security Risks.
- Mobile applications. We evaluate the security level of a mobile app following OWASP Top 10 Mobile Risks.
- Desktop applications. We assess how data is stored in an app, how this app transfers information, whether any authentication is provided.
Assessment Methods We Apply
Our security testing team combines automated and manual approaches to take the full advantage of the vulnerability assessment process.
Automated scanning
To start the vulnerability assessment process, Fuzzsecurity engineers use automated scanning tools the choice of which depends on your requirements and financial capabilities. These scanners have databases, which contain known technical vulnerabilities and allow detecting your company’s susceptibility to them.
The main advantage of this approach is that it is not time-consuming and ensures a wide coverage of security weaknesses.
Manual assessment
Fuzzsecurity testing team performs the manual tuning of the scanning tools, as well as subsequent manual validation of the scanning findings to eliminate false positives.
Upon the completion of such manual assessment, you get reliable results containing only confirmed events.
Vulnerabilities Classification Techniques We Apply
When conducting vulnerability assessment, we divide the detected security weaknesses into groups according to their type, severity level, etc. following the classifications below.
- Web Application Security Consortium (WASC) Threat Classification.
- Open Web Application Security Project (OWASP) Testing Guide.
- OWASP Top 10 Application Security Risks.
- OWASP Top 10 Mobile Risks.
- Common Vulnerability Scoring System (CVSS).
Classifying vulnerabilities allows Fuzzsecurity engineers to prioritize the findings according to the impact they may have in case of exploitation and direct your attention to the most critical weaknesses that need to be eliminated on a first-priority basis to avoid financial and security risks.